Cybersecurity Solution
our capabilities
These are outcome-focused, one-time implementations that secure digital assets, infrastructure, and data through strategy, tools, and technologies tailored to an organization’s specific threat landscape and compliance needs.


Security Infrastructure Implementation
Deployment of essential cybersecurity components like firewalls, IDS/IPS, and endpoint protection.
Recent Project
Implementing a multi-layered perimeter security setup with next-gen firewall and intrusion detection for a growing SaaS company.
Network Segmentation & Access Control Solution
Designing secure, segmented networks with role-based access controls to prevent lateral threats.
Recent Project
VLAN segmentation for an enterprise environment to isolate sensitive departments like finance and HR.
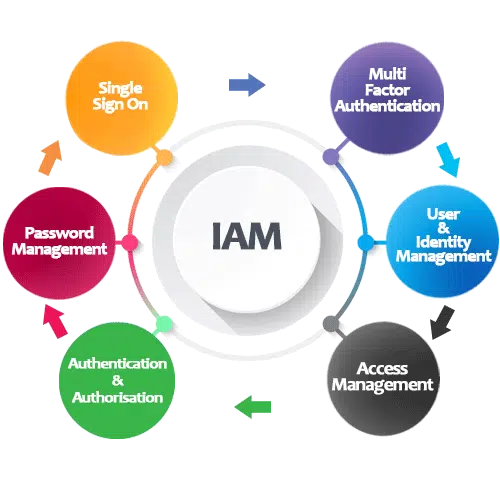
Identity & Access Management (IAM) Deployment
Implementation of centralized user authentication, authorization, and identity lifecycle management.
Recent Project
Integrating SSO and MFA with Okta for all enterprise applications and directory services.
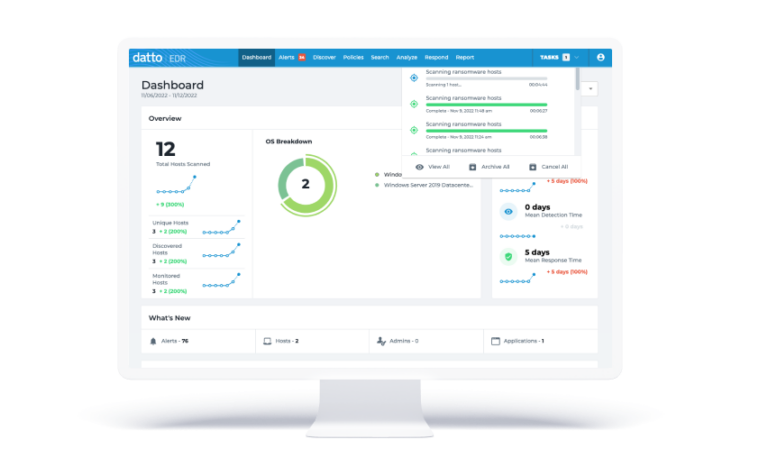
Endpoint Detection & Response (EDR) Deployment
Installing and configuring EDR solutions across all organizational endpoints.
Recent Project
Rolling out CrowdStrike or SentinelOne across 1,000+ devices with centralized threat monitoring.

Cloud Security Posture Hardening
Securing cloud environments through configuration, encryption, and threat prevention mechanisms.
Recent Project
AWS environment audit and remediation for public S3 buckets, exposed ports, and IAM misconfigurations.
Vulnerability Assessment & Remediation Solution
End-to-end deployment of scanning tools with remediation of discovered vulnerabilities.
Recent Project
Implementing a quarterly scan policy and patching workflow using Qualys or Nessus.
Zero Trust Architecture Implementation
Deployment of a zero-trust model across networks, users, and applications.
Recent Project
Application-level access controls and identity verification before every access request within a distributed enterprise.
Security Information & Event Management (SIEM) Solution
Implementation of a centralized platform for logging, monitoring, and real-time security alerts.
Recent Project
Deploying Splunk or Azure Sentinel to monitor all network and server activities.

Data Loss Prevention (DLP) Setup
Deployment of tools to detect and block sensitive data from unauthorized transfer or leakage.
Recent Project
Installing Microsoft Purview DLP to monitor and restrict email or file-sharing of confidential documents.
Cybersecurity Risk Assessment & Strategy Design
Conducting a structured risk analysis followed by the creation of a cybersecurity roadmap.
Recent Project
A gap analysis and control framework design for a fintech startup planning to scale operations globally.

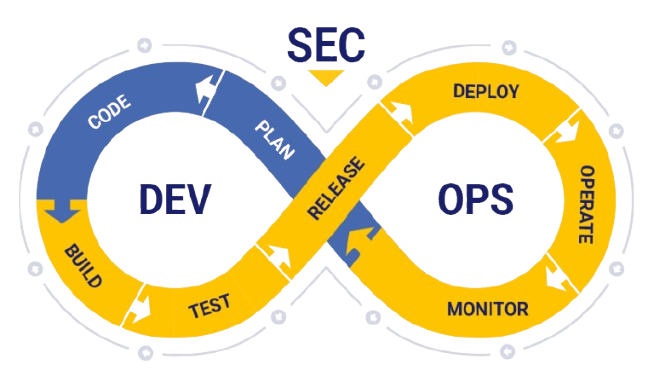
Application Security Solution (DevSecOps)
Securing software development processes through code scanning, threat modeling, and CI/CD integration.
Recent Project
Integrating SAST and DAST tools into a DevOps pipeline using GitHub Actions and SonarQube.
Email Security Gateway Implementation
Deployment of secure email gateways and anti-phishing tools to protect enterprise communication.
Recent Project
Implementing Mimecast or Proofpoint to block phishing, spoofing, and malware-laced attachments.
Secure Remote Access & VPN Deployment
Designing a secure, encrypted access solution for remote workers and external vendors.
Recent Project
Configuring SSL VPN with device posture checks and geo-restrictions for third-party access.
Incident Response & Forensics Readiness Framework
Creating a structured response plan and forensics system to investigate cyber incidents.
Recent Project
Building an IR plan with escalation matrix, threat hunting toolkit, and legal audit trail logging.
Security Compliance Enablement Solution
Aligning IT systems and documentation with regulatory standards like ISO 27001, GDPR, or PCI-DSS.
Recent Project
A project to prepare and certify an eCommerce company for PCI-DSS through system hardening and policy implementation.
These Cybersecurity Solutions are strategically scoped, tailored, and executed as complete projects, ensuring organizations gain hardened security postures, minimized risks, and compliance with critical standards not ongoing managed services.
Feel exposed to cyber risks? Shield your business with our expertise.

One Stop Solution Served With Vision & Care
